There's a good chance that the password on your streaming service sucks
A study on password stuffing finds 'entertainment sites' are far more likely to reuse breached credentials
Three things that should be taught in school: Sex-ed, basic personal finance, and good password hygiene. Sadly, at least for those of us here in the United States, all three are sorely lacking.
The latter point was laid bare in a study from members of Google's Spam and Abuse Research Team. Too many passwords are being reused — and that opens the users to credential stuffing, which is where a bad actor tries a username and password combination leaked from one service on all kinds of other services, just to see if they'll work.
Or, to put it simply, if your Netflix email and password is the same as the what you used for MySpace and was part of that 360 million-account breach, there's a good chance someone can get into your Netflix account if they want.
Just because it's not as "important" as your bank doesn't mean it doesn't need a good password.
The researchers (which also included one from Stanford University) came to their conclusions from Google Chrome's Password Checkup extension, which securely checks passwords saved in Chrome with more than 4 billion unsafe username and password combinations that were at some point caught up in a breach.
The pattern of behavior shouldn't be terrible surprising. Big targets like banks and other financial institutions would more typically have strong, unique passwords. Softer targets like streaming services and other entertainment sites (and, I'd wager, things that you might also log in to from some sort of TV remote control) pinged the list of unsafe logins far more often.
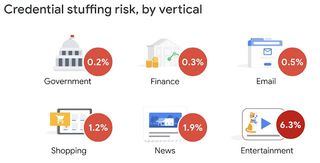
How much more often? The nine entertainment sites listed in the study (they didn't say which ones) made up just 0.8 percent of the total number of visits, but accounted for 6.3 percent of the warnings. The next highest warning rate was "adult" websites at 3.6 percent. (Which made up just 0.2 percent of the total number of visits. Seems low, but whatever.)
The scarier number is the "ignore rate," which means users were warned that their passwords potentially had been breached at some point — but they chose not to change them. Adult sites made up 38.5 percent of ignored warnings, and entertainment sites were second at 27.1 percent.
Here's how things were put in the study, which you can read in its entirety here as a pdf :
Domains that we categorized as related to finance or governments exhibited the lowest rate of reused, breached credentials (0.2–0.3%). Possible explanations include the password composition policies of these domains, the fact that users adhere to popular security advice to have one strong password for their bank, or that the sites actively identify breaches and previously forced password resets.
In contrast, entertainment sites like streaming video platforms and adult websites had the highest warning rate for breached credentials (3.6–6.3%). Users may adopt disposable passwords due to perceived lack of risk, or in the case of streaming sites, they may use shared accounts. Surprisingly, users ignored our breach warnings nearly uniformly across categories, with the exception of adult websites. For the latter, users ignored nearly twice as many of our warnings—potentially to hide the domain from our persistent warning tray.
That bit about "perceived lack of risk" is interesting. As far as I'm concerned, a password is a password is a password. I also strongly believe that we tend to look at security completely wrong. We tend to trust the services we use, considering them to be secure until proven otherwise. That's backward. We should assume everything we do — every new service we sign up for, every new. credential — can and will be breached, and we should do whatever we can to mitigate that risk.
Strong, unique passwords are the first step in that fight. You can use what's built in to your browser, or you can use a third-party password manager. Here are but a few that are worth exploring:
And you absolutely should use two-factor authentication whenever possible. Hardware keys are best , though I can't think of a single streaming service that uses them. (Save for, I suppose, YouTube TV, since it uses your Google login.) Software tokens are OK, but they can be spoofed. Time-based SMS codes should be avoided if at all possible.
And employ a service like Google Chrome's Password Checkup extension , or the Have I Been Pwned? service to see if your credentials have been caught up in a breach.
But as often is the case, the simplest solution may well be the best one: Don't reuse passwords. And if something warns you that your Netflix password may have been breached somewhere else, it's time to change it.
Get the What to Watch Newsletter
The latest updates, reviews and unmissable series to watch and more!
